IT运维笔记
SQLSERVER修改密码提示错误2812:未能找到存储过程'sppassword'解决方法
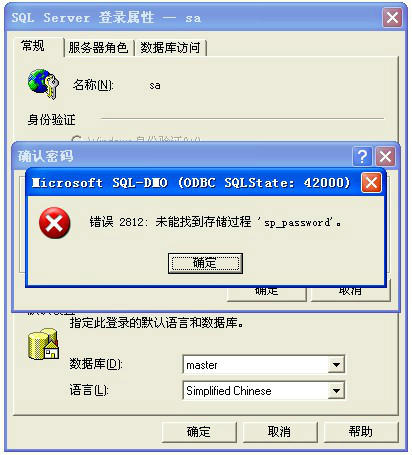
问题分析:因 sql 服务器中毒,导致病毒篡改 sql 用户的密码,病毒为了阻止操作员手工修正(修改)sql用户的密码,而把存储过程 'sp_password' 删除,导致的问题。错误如下图所示:
 解决思路:在系统中重新建一个 'sp_password' 的存储过程,以便更新现有的 sql用户密码
步骤:
1、打开查询分析器:
方法1. 可以依次打开:开始---> 运行 ,输入命令 isqlw,按回车即可启动查询分析器
方法2. 通过开始菜单、程序、microsoft sql server、找到“查询分析器”单击打开即可启动
2、登录 查询分析器:在弹出的登录界面中作如下图所示的设置,点“确定”,登录到查询分析器中
解决思路:在系统中重新建一个 'sp_password' 的存储过程,以便更新现有的 sql用户密码
步骤:
1、打开查询分析器:
方法1. 可以依次打开:开始---> 运行 ,输入命令 isqlw,按回车即可启动查询分析器
方法2. 通过开始菜单、程序、microsoft sql server、找到“查询分析器”单击打开即可启动
2、登录 查询分析器:在弹出的登录界面中作如下图所示的设置,点“确定”,登录到查询分析器中
 3、把下面附录中的重建代码复制到刚才打开的查询分析器中
4、按 f5 执行重建代码
代码分析:允许修改系统数据 ---> 重建系统内置存储过程 ----> 恢复为不能直接修改系统数据
5、后记:此方法只是能解决因为没有存储过程而不能修改密码的问题
附录:重建 sp_passsword 存储过程 代码
3、把下面附录中的重建代码复制到刚才打开的查询分析器中
4、按 f5 执行重建代码
代码分析:允许修改系统数据 ---> 重建系统内置存储过程 ----> 恢复为不能直接修改系统数据
5、后记:此方法只是能解决因为没有存储过程而不能修改密码的问题
附录:重建 sp_passsword 存储过程 代码
 解决思路:在系统中重新建一个 'sp_password' 的存储过程,以便更新现有的 sql用户密码
步骤:
1、打开查询分析器:
方法1. 可以依次打开:开始---> 运行 ,输入命令 isqlw,按回车即可启动查询分析器
方法2. 通过开始菜单、程序、microsoft sql server、找到“查询分析器”单击打开即可启动
2、登录 查询分析器:在弹出的登录界面中作如下图所示的设置,点“确定”,登录到查询分析器中
解决思路:在系统中重新建一个 'sp_password' 的存储过程,以便更新现有的 sql用户密码
步骤:
1、打开查询分析器:
方法1. 可以依次打开:开始---> 运行 ,输入命令 isqlw,按回车即可启动查询分析器
方法2. 通过开始菜单、程序、microsoft sql server、找到“查询分析器”单击打开即可启动
2、登录 查询分析器:在弹出的登录界面中作如下图所示的设置,点“确定”,登录到查询分析器中
 3、把下面附录中的重建代码复制到刚才打开的查询分析器中
4、按 f5 执行重建代码
代码分析:允许修改系统数据 ---> 重建系统内置存储过程 ----> 恢复为不能直接修改系统数据
5、后记:此方法只是能解决因为没有存储过程而不能修改密码的问题
附录:重建 sp_passsword 存储过程 代码
3、把下面附录中的重建代码复制到刚才打开的查询分析器中
4、按 f5 执行重建代码
代码分析:允许修改系统数据 ---> 重建系统内置存储过程 ----> 恢复为不能直接修改系统数据
5、后记:此方法只是能解决因为没有存储过程而不能修改密码的问题
附录:重建 sp_passsword 存储过程 代码
sp_configure 'allow updates', 1
reconfigure with override
go
use master
go
if exists (select * from dbo.sysobjects where id = object_id(n'[dbo].[sp_password]') and objectproperty(id, n'isprocedure') = 1)
drop procedure [dbo].[sp_password]
go
create procedure sp_password
@old sysname = null, -- the old (current) password
@new sysname, -- the new password
@loginame sysname = null -- user to change password on
as
-- setup runtime options / declare variables --
set nocount on
declare @self int
select @self = case when @loginame is null then 1 else 2 end
-- resolve login name
if @loginame is null
select @loginame = suser_sname()
-- check permissions (securityadmin per richard waymire) --
if (not is_srvrolemember('securityadmin') = 1)
and not @self = 1
begin
dbcc auditevent (107, @self, 0, @loginame, null, null, null)
raiserror(15210,-1,-1)
return (1)
end
else
begin
dbcc auditevent (107, @self, 1, @loginame, null, null, null)
end
-- disallow user transaction --
set implicit_transactions off
if (@@trancount > 0)
begin
raiserror(15002,-1,-1,'sp_password')
return (1)
end
-- resolve login name (disallows nt names)
if not exists (select * from master.dbo.syslogins where
loginname = @loginame and isntname = 0)
begin
raiserror(15007,-1,-1,@loginame)
return (1)
end
-- if non-sysadmin attempting change to sysadmin, require password (218078) --
if (@self <> 1 and is_srvrolemember('sysadmin') = 0 and exists
(select * from master.dbo.syslogins where loginname = @loginame and isntname = 0
and sysadmin = 1) )
select @self = 1
-- check old password if needed --
if (@self = 1 or @old is not null)
if not exists (select * from master.dbo.sysxlogins
where srvid is null and
name = @loginame and
( (@old is null and password is null) or
(pwdcompare(@old, password, (case when xstatus&2048 = 2048 then 1 else 0 end)) = 1) ) )
begin
raiserror(15211,-1,-1)
return (1)
end
-- change the password --
update master.dbo.sysxlogins
set password = convert(varbinary(256), pwdencrypt(@new)), xdate2 = getdate(), xstatus = xstatus & (~2048)
where name = @loginame and srvid is null
-- update protection timestamp for master db, to indicate syslogins change --
exec('use master grant all to null')
-- finalization: return success/failure --
if @@error <> 0
return (1)
raiserror(15478,-1,-1)
return (0) -- sp_password
go
sp_configure 'allow updates', 0
reconfigure with override